No products in the cart.
Course summary
Certified Ethical Hacker offers a balanced blend of knowledge-based training and hands-on labs. This all takes place in a virtual environment with live targets as well as the latest in AI tools, techniques, and systems.
- 100% visualization with full access to pre-configured targets, networks, and attack tools
- Pre-configured vulnerable websites o Vulnerable, unpatched operating systems
- Fully networked environments of 4000+ hacking tools
- Wide range of target platforms to hone your skills, with 550 attack techniques covered
- Objective-oriented flags for critical thinking and applied knowledge assessment
- Cloud-based cyber range
Who is a Certified Ethical Hacker?
A Certified Ethical Hacker is a specialist typically working in a red team environment, focused on attacking computer systems and gaining access to networks, applications, databases, and other critical data on secured systems. A C|EH® understands attack strategies and the use of creative attack vectors and mimics the skills and creativity of malicious hackers. Unlike malicious hackers and actors, Certified Ethical Hackers operate with permission from the system owners and take all precautions to ensure the outcomes remain confidential. Bug bounty researchers are expert ethical hackers who use their attack skills to uncover vulnerabilities in the systems.
What’s new for version 13
- AI-powered
The world’s first ethical hacking program to harness the power of AI.
- Hands-on experience
Cybersecurity professionals can hone their skills in real-world scenarios through hands-on labs. Here, they’ll practice attack vectors and master advanced hacking tools.
- 40% more efficient
Learn AI-driven techniques to boost 40% more efficiency in cyber defense while streamlining workflows.
- Power-packed, updated curriculum
Master the latest advanced attack techniques, trends, and countermeasures.
- 2x productivity gains
Advanced threat detection, enhanced decision-making, adaptive learning, enhanced reporting, and automation of repetitive tasks.
- Real-world skills, proven mastery
Participate in monthly global hacking competitions, compete with peers, and make it onto the leaderboard.
Learning Program
- 5 days of training
- 20 modules
- 91 Core Labs + 130 Self-study Labs*
- 3000+ Student Manual Pages
- Learn how to hack multiple operating systems
- (Windows 11, Windows servers, Linux,
- Ubuntu, Android)
- MITRE Attack Framework
- Diamond model of intrusion analysis
- Techniques for establishing persistence
- Evading NAC and endpoint security
- Understand Fog, Edge, and Grid Computing Model
C|EH v13 – Inclusions & Validity
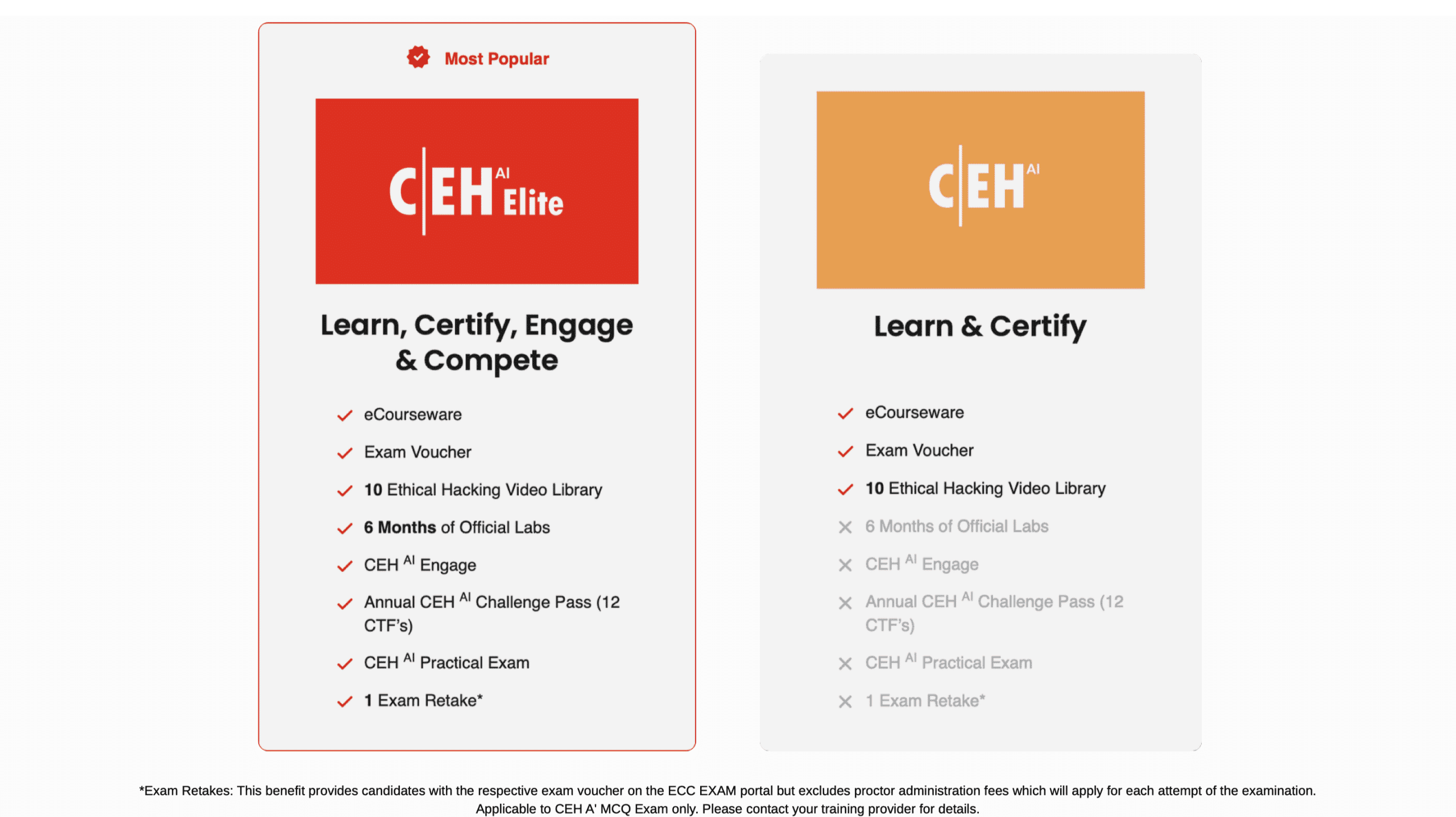
| Inclusions | Lite Package Validity | Elite Package Validity |
|---|---|---|
| eCourseware | 2 years | 2 years |
| Exam Voucher | 1 year | 1 year |
| Ethical Hacking Videos | 1 year | 1 year |
| Exam Retakes | ✗ | 1 |
| EC-Council Labs | ✗ | 6 months |
| C|EH Engage | ✗ | 1 year |
| Global C|EH Challenge | ✗ | 1 year |
| C|EH Practical | ✗ | 1 year |
CEH Exam
The C|EH® exam is a 4-hour exam with 125 multiple-choice questions. This knowledge-based exam will test our skills in information security threats and attack vectors, attack detection, attack prevention, procedures, methodologies, and more!
Course Outline
From the creators of Certified Ethical Hacker (CEH) comes the new and evolved version 13 with added AI capabilities. Structured across 20 learning modules covering over 550 attack techniques, CEH provides the core knowledge needed to thrive as a cybersecurity professional.
- Module 01: Introduction to Ethical Hacking
- Module 02: Footprinting and Reconnaissance
- Module 03: Scanning Networks
- Module 04: Enumeration Module
- Module 05: Vulnerability Analysis
- Module 06: System Hacking
- Module 07: Malware Threats
- Module 08: Sniffing
- Module 09: Social Engineering
- Module 10: Denial-of-Service
- Module 11: Session Hijacking
- Module 12: Evading IDS, Firewalls, and Honeypots
- Module 13: Hacking Web Servers
- Module 14: Hacking Web Applications
- Module 15: SQL Injection
- Module 16: Hacking Wireless Networks
- Module 17: Hacking Mobile Platforms
- Module 18: IoT Hacking
- Module 19: Cloud Computing
- Module 20: Cryptography
Which certification is best for hacking?
The CEH program helps you understand hackers by getting you into their mindset. After all, to be a kicker, you need to think like a hacker. There are both unethical and ethical hackers: unethical hackers engage in illegal or unlawful activities, while ethical hackers use their hacking knowledge to protect organizations and their assets. The official C|EH course is the world’s #1 ethical hacking certification. If you want to become one of the world’s best ethical hackers, the C|EH is recommended by experienced professionals, organizations in both the private and public sectors, industry leaders and experts, and hiring managers.
Prerequisites for Certified Hacker Program
There are no specific prerequisites for the Certified Hacker Program; however, we strongly recommend candidates possess a minimum of 2 years’ experience in IT security before joining a CEH training program. CEH training is about testing systems and using them for purposes not originally intended; candidates should understand the basic functions of those IT systems before attempting to hack them. (Example: CEH will teach the process of host evaluation leading to enumeration; in this process trainees will scan downrange targets using common scanning techniques such as Nmap which will respond with a list of ports, enumerating those ports and the services running on them can be used to expose common vulnerabilities and weaknesses in systems. The CEH program will not teach you what a port is, that is essential knowledge you must have to be successful in the class.)
Open AI credits
- Open AI credits are not included in the program, since Open Ai owns proprietary technology, it is necessary to purchase license keys with credits.
- Prospective students who wish to use this technology in the classroom must purchase OpenAI API credits to perform ShellGPT labs in the classroom.
- Each partner has the option to require each student to purchase the licenses individually or to purchase the licenses for a specific class (estimated costs are under $1 per student, per CEH class).
Who CEH v13 is for
Cybersecurity professionals
Those looking to drive their cybersecurity career forward with the power of AI.
Teams and organizations
Teams looking to turbocharge their AI knowledge in order to stay one step ahead of malicious actors.
Government and military
Government departments and defense bodies looking for a trusted and highly valued global certification partner.






















